Solution Service
SOLUTION SERVICE
SIP/VoIP Security Audit
- Service Overview
-
Nextgen IMS (IP Multimedia Subsystem) / VoLTE (Voice over LTE) Security Audit Service is a vital step in the project lifecycle of telecom operators who are offering IMS related services such as VoLTE and VoWiFi (Voice over Wi-Fi). It helps telecom operators to achieve the highest degree of robustness of IMS and VoLTE systems, and keeps the systems safe from the threats in a proactive fashion. The vendor independent service - the professional service offering from Nextgen's IMS/VoLTE security experts - develops a detailed analysis based on industry standards and best practices in order to make the systems and networks entirely secure. The analysis identifies vulnerabilities of the systems through more than 6 million test cases, assesses the severity of the vulnerabilities based on CVSS (Common Vulnerability Scoring System) standard, and provides comprehensive set of recommendations - including systems configuration optimizations, bug fixes, improvement of security guidelines, and so forth.
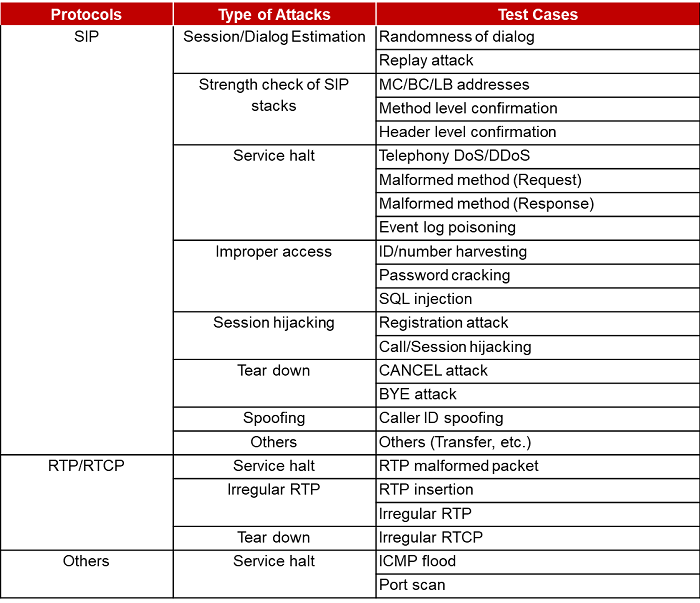
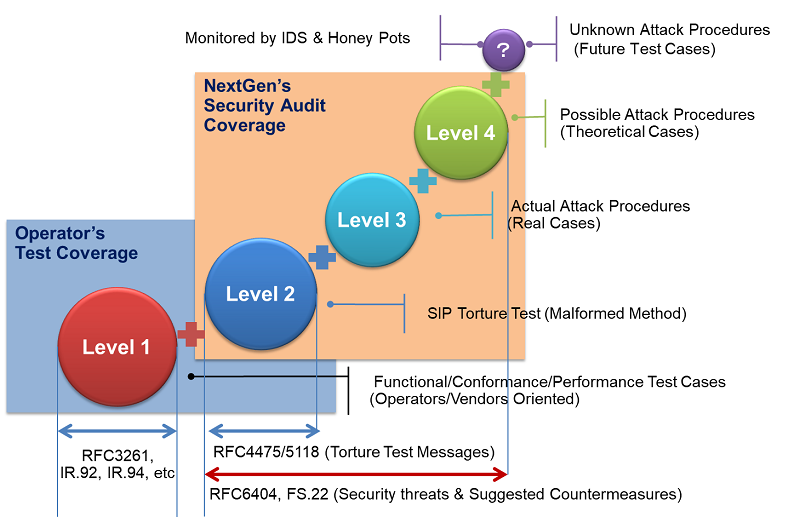
Noteworthy the difference between this IMS/VoLTE Security Audit and that of other 3rd party's is the in-depth coverage of security testing. Telecom operators, network systems vendors, and test equipment vendors validate protocol conformance, interoperability, performance, and regressions, and at the most do the penetration testing for the purpose of robust protection. Our IMS/VoLTE Security Audit is highly advanced and mature from the network security perspective. In general, penetration testing is performed based on the industry standards torture test messages like IETF (Internet Engineering Task Force) RFC4475 and RFC5118. These are only part of our security audit framework whereas the framework covers even sophisticated attacks based on RFC6404 and GSMA PRD FS.22, real threats in the live networks, and theoretical cases.
Benefits
The IMS/VoLTE Security Audit Service offers the proactive protection of IMS core network from a wide range of threats in order to ensure services continuity, minimize business risk, and maximize return on investments and business opportunities.
Telecom operators do not have to have expertise in specialized security area, to keep track of the latest intruders, nor to have pseudo-environments for the security testing. They only have to control security policies, processes, procedures, organizational structures, and software and hardware functions, where necessary, to ensure the specific security and business objectives are met.
Vendor independent 3rd party testing is also beneficial to telecom operators because they can consider the findings objectively and improve systems quality.
- Audit for
-
・Telecom Carriers
・Mobile Operators
・VoIP/IMS System Vendors
・VoIP/IMS System Integrators
・VoIP/IMS System Integrators
- Diagnosis Target for (Any system using SIP)
-
・Unified Communications Server
・IMS/NGN SIP servers (CSCF)
・Session Border Controller (SBC)
・SIP-NAT system
・IP-PBX
・VoIP GW
・SIP Phones
・M2M Systems
・IM/Presence system
- Testing Protocol (IPv4 and IPv6 support)
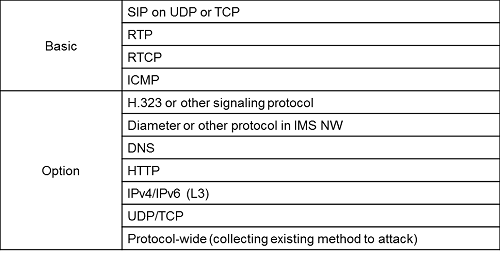
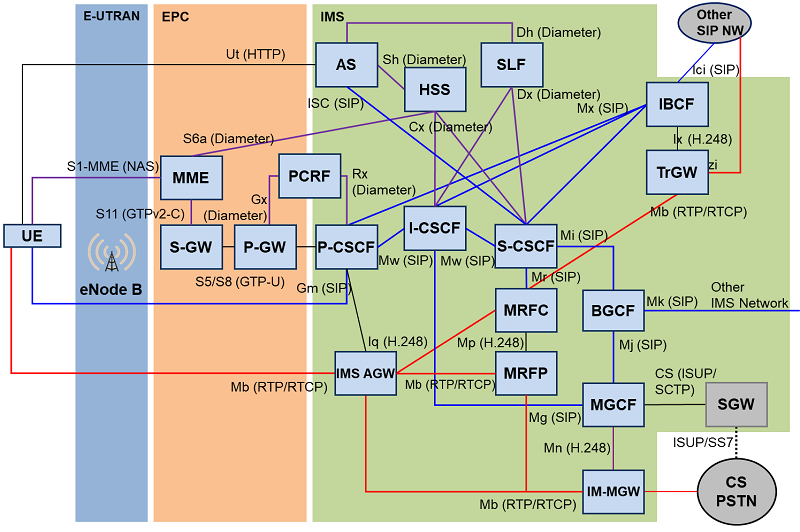
Scope of IMS/VoLTE Security Audit
IMS core nodes, EPC nodes, and user-side devices are all within the scope of our IMS/VoLTE Security Audit service. Objective of the Standard Audit service includes SIP aware IMS core nodes and devices, and the Optional Audit service covers Diameter aware IMS core and EPC nodes in order to meet the specific customer requirements. Customers may choose one or more system objectives for the audit.
Security Audit Methodologies
The IMS/VoLTE Security Audit service can be divided into two types of testing methodologies – System Unit Testing and Route Testing. Customers may choose either one or both, depending on their level of concern.
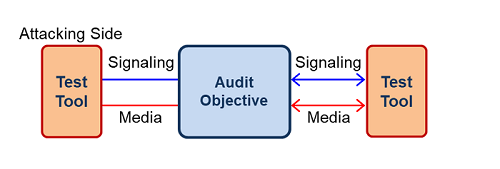
1. System Unit Testing
The System Unit Testing is a method by which individual units of IMS/EPC nodes or devices together with associated security
configurations are verified to determine if the individual node is fully secure for commercial use. The objective of the System
Unit Testing is to isolate a unit and validate its confidentiality, integrity, and availability at the system side.
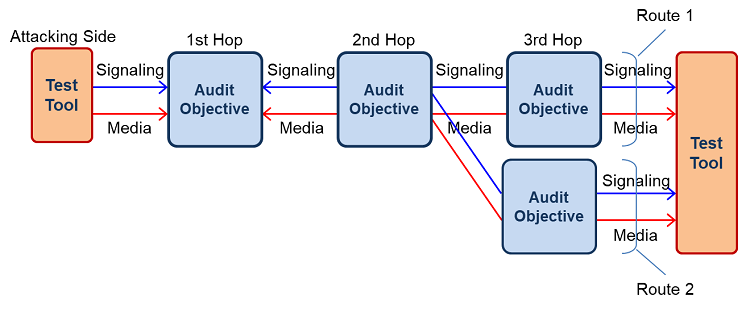
2. Route Testing
The Route Testing is a method by which multiple collaborative nodes in the same environment together with associated security
configurations are verified to determine if the entire network or service is fully secure for commercial use.The objectives of the
Route Testing are in-line and validate confidentiality, integrity, and availability at the services level.
1. System Unit Testing
The System Unit Testing is a method by which individual units of IMS/EPC nodes or devices together with associated security
configurations are verified to determine if the individual node is fully secure for commercial use. The objective of the System
Unit Testing is to isolate a unit and validate its confidentiality, integrity, and availability at the system side.

2. Route Testing
The Route Testing is a method by which multiple collaborative nodes in the same environment together with associated security
configurations are verified to determine if the entire network or service is fully secure for commercial use.The objectives of the
Route Testing are in-line and validate confidentiality, integrity, and availability at the services level.

Security Audit Process
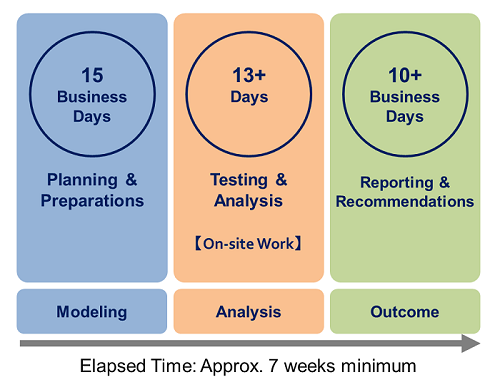
1. Planning & Preparation
The planning and preparation before commencing IMS/VoLTE Security Audit involve approximately 3-weeks with the following activities:
a. Customer to decide the scope of IMS/VoLTE Security Audit
・System & Protocol objectives
・Audit methodology
b. Customer to make a baseline survey of the audit objectives based on NextGen’s survey form
・Customer proprietary protocol specifications and standards conformity
・Network topology and optionally services specifications
・Policies, KPIs, products, features, and configurations regarding IMS/VoLTE security
・etc.
c. Customer to arrange the test bed resources
d. NextGen to customize/configure its test tools
e. Customer to set up the test bed environments
・Ethernet ports for NextGen’s tools
・User accounts under test
・Node for routing, authentication, etc.
・Simulators (as necessary)
・Monitors for error logs or alarms (NMS/EMS)
2. Security Audit Testing & Analysis
NextGen’s security professionals test IMS related systems on-site at customer’s lab to determine if any potential security
problem exist in the system, then let the customer determine which of the security problems should be fixed. Once determined,
the customer will make the necessary system changes for resolution.
The reference running time of the standard test case for a single audit objective is as follows:
・Total of 13 days (300 hours), 24 hours a day, 7 days a week
・Automated testing runs 12 or 14 hours a day, 7 days a week
・Manual testing runs 8 or 10 hours a day, 5 days a week
Our testing monopolizes the security audit objectives during minimum of 17 hours and 2 days at maximum. Except for high risk
attack testing such as massive messages DoS, port scanning, and ICMP flooding, we can share the same environment with
the customer.
3. Audit Report and Recommendations
Upon completion of the Security Audit test, NextGen’s security professionals will analyze the details and issue a report which covers
findings with CVSS scores as well as advise the modifications of system configurations, bug fixes, additions and improvements of
security products.
Deliverables
1. Daily Event Report
During the Security Audit, we document a daily event report on the audit progress and detected vulnerabilities. With this event report,
operators can immediately address the issues in collaboration with the relevant vendor personnel.
2. Final Security Audit Report
The final report covers a comprehensive set of recommendations on how the system should work at system/services level.
The report includes:
a. Outline of IMS/VoLTE security audit
b. Interview sheet (if any)
c. Test cases & Summary of outcomes
d. List of findings (Severity of vulnerabilities & Suggested countermeasures)
e. Test cases & Detailed outcomes
f. Security audit environments
3. Test Logs
Vulnerability related log files during the security audit are also provided to help operators and vendors reproduce and fix the detected problem.
During the Security Audit, we document a daily event report on the audit progress and detected vulnerabilities. With this event report,
operators can immediately address the issues in collaboration with the relevant vendor personnel.
2. Final Security Audit Report
The final report covers a comprehensive set of recommendations on how the system should work at system/services level.
The report includes:
a. Outline of IMS/VoLTE security audit
b. Interview sheet (if any)
c. Test cases & Summary of outcomes
d. List of findings (Severity of vulnerabilities & Suggested countermeasures)
e. Test cases & Detailed outcomes
f. Security audit environments
3. Test Logs
Vulnerability related log files during the security audit are also provided to help operators and vendors reproduce and fix the detected problem.
Standard Test Case